The Average Company Wastes 37% of Its Software Budget
Quick question: how many software tools does your business pay for right now? Follow-up question: how many are actually being used? According to an...
Prevent Leaking Private Data Through Public AI Tools
Public AI tools are powerful, but they come with real risk. Most use the data entered into them to train and improve their models. That means...
Tools You Never Knew Existed but Can’t Live Without: Emoji and Symbols Panel
Some people think emojis are just for their phones. What’s easy to miss is that Windows has a built-in emoji and symbols panel you can open anywhere...
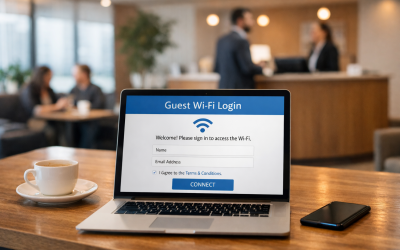
Securing Your Office Guest Wi-Fi
Guest Wi-Fi is a convenience visitors expect and a sign of good customer service. It’s also one of the riskiest entry points into your network. A...
Why You Should Treat Your Passwords Like Underwear
When it comes to cybersecurity, one quirky but effective analogy is: treat your passwords like underwear. It might sound funny, but the comparison...
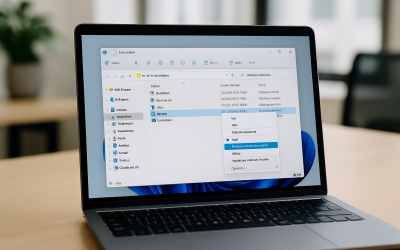
Tools You Never Knew Existed but Can’t Live Without: File Version History
We have all been there. You open a file, make a quick change, save it without thinking, and then realize you need the previous version back. Maybe...
How to Use Virtual Cards for Low-Risk Holiday Shopping
Have you ever been concerned about your credit card or personal data getting stolen while shopping online? You’re not alone. Each holiday season, as...
Merry Christmas – From Wingman IT Services
Merry Christmas! From your team at Wingman IT Services Andrew, Stacey, Steve, Marc, Alex, Leigh, Bob, and Sarah
Navigating Cloud Compliance
Cloud solutions are the technology darlings of today’s digital landscape. They offer a perfect balance of innovation and organizational efficiency,...
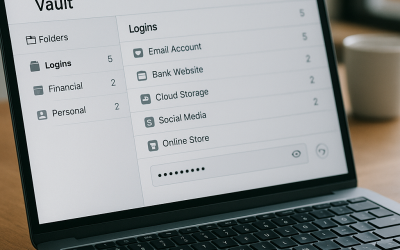
Advanced Strategies to Lock Down Your Business Logins
Good login security works in layers. The more barriers you add, the less likely attackers are to reach your data. Strengthen Passwords and...